Proxy
Proxy servers act as relay machines between clients and applications servers. Having a machine acting as a gateway protects clients and/or servers from being seen directly from the other parts. The type of server is defined by its position: a forward proxy, aka proxy, sits in front of clients and a reverse proxy is placed in front of servers.
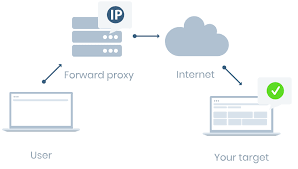
Forward Proxy
The forward proxy acts a a relay for clients; it intercepts all outgoing requests and forwards it to the destination servers with its own IP address. The clients stay anonymous to the servers. Before forwarding the requests, proxies can perform operations such as authenticating the clients, authorizing the traffic to be forwarded or not and also apply filters on accessible resources. It can also act as a cache server some frequent requests in order to improve performance.
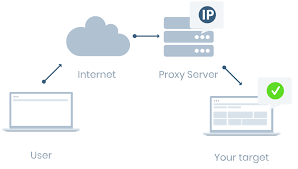
Reverse Proxy
The Reverse Proxy acts as an intermediary servers for all incoming requests to servers; its protects the servers from being seen directly. Services may sit on different physical servers while the clients get connected to the same URL or IP address. In addition to authentication/authorization process, the reverse proxy can also load balance the traffic towards multiple destination servers depending on predefined rules: URL, number of sessions, redundancy…
Configuration
A Synology NAS can host multiple services which are reachable on a unique IP address but different ports or different IP address. Configuring Reverse Proxy rules are then required to steer the traffic and forward it accordingly.
For example, the Synology can host a WordPress site www.siteA.com, a Matrix chat server matrix.mydomain.com and Bitwarden Password Manager. All incoming traffic must be redirected to the correct service:
- all traffic with destination https://www.siteA.com will be redirected to my web station http://localhost:8080
- all traffic with destination https://bitwarden.mydomain.com is forwarded to http://localhost:5151
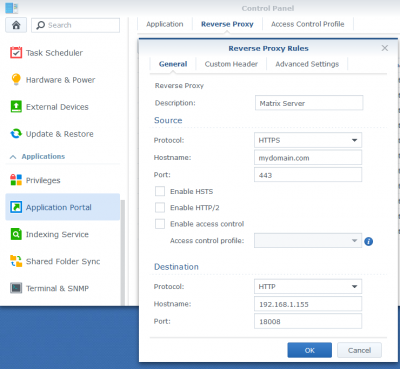
- all traffic with destination https://mydomain.com will be redirected to my Synapse server http://192.168.1.155:18008 (as shown below)
Reverse Proxy rules can be configured Control Panel / Application Portal / Reverse Proxy tab:
NGINX
Synology Reverse Proxy is based on Nginx engine. Configuration done in GUI is written in a file located at /etc/nginx/app.d/server.ReverseProxy.conf.
If you need more fine parameters than the ones you can set via the GUI, you can create a rule manually creating a file named mydomain.com saved in /usr/local/etc/nginx/sites-enabled. This rule won’t appear in the Application Portal GUI. Here is an example of rule created for Matrix Messaging:
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name mydomain.com;
ssl_certificate /path_to_your_domain_certificate/fullchain.pem;
ssl_certificate_key /path_to_your_domain_certificate/privkey.pem;
location ~* ^(\/_matrix|\/_synapse|\/_synapse\/admin|\/client) {
proxy_connect_timeout 60;
proxy_read_timeout 60;
proxy_send_timeout 60;
proxy_intercept_errors off;
proxy_http_version 1.1;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://localhost:18008;
}
location /.well-known/matrix/server {
default_type application/json;
return 200 '{ "m.server": "mydomain.com:443" }';
add_header Content-Type application/json;
add_header Access-Control-Allow-Origin *;
}
error_page 403 404 500 502 503 504 @error_page;
location @error_page {
root /usr/syno/share/nginx;
rewrite (.*) /error.html break;
allow all;
}
}Once configured with root privileges (“sudo su -“), run the following commands:
- nginx -T > /tmp/nginx.conf to test if the configuration works
If no error is returned, apply it:
- nginx -s reload