HTTP from the beginning
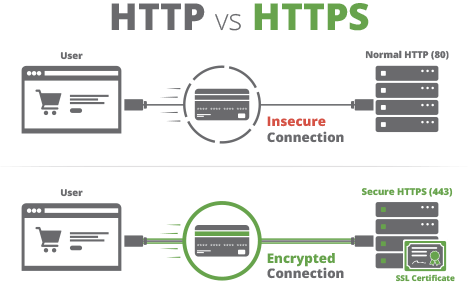
Since the beginning of the www, HTTP (Hyper Text Transfer Protocol) is the most commonly protocol used between clients and servers. Despite multiple evolutions, one thing never changes from the beginning: data is carried unencrypted meaning that anyone sniffed the flows can access to your information.
Evolution to HTTPS
Hypertext transfer protocol secure (HTTPS) is the secure version of HTTP, which is the primary protocol used to send data between a web browser and a website. HTTPS is encrypted in order to increase security of data transfer. This is particularly important when users transmit sensitive data, such as by logging into a bank account, email service, or health insurance provider.
Any website, especially those that require login credentials, should use HTTPS. In modern web browsers such as Chrome, websites that do not use HTTPS are marked differently than those that are. Look for a green padlock in the URL bar to signify the webpage is secure. Web browsers take HTTPS seriously; Google Chrome and other browsers flag all non-HTTPS websites as not secure.
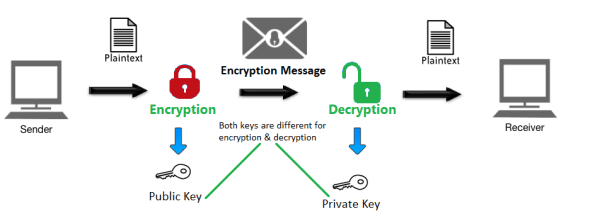
HTTPS uses an encryption protocol to encrypt communications. The protocol is called Transport Layer Security (TLS), although formerly it was known as Secure Sockets Layer (SSL). This protocol secures communications by using what’s known as an asymmetric public key infrastructure. This type of security system uses two different keys to encrypt communications between two parties:
The private key – this key is controlled by the owner of a website and it’s kept, as the reader may have speculated, private. This key lives on a web server and is used to decrypt information encrypted by the public key.
The public key – this key is available to everyone who wants to interact with the server in a way that’s secure. Information that’s encrypted by the public key can only be decrypted by the private key.
SSL Certificate creation
Prerequisite to SSL creation is having port 80 and 443 forwarded to the Synology.
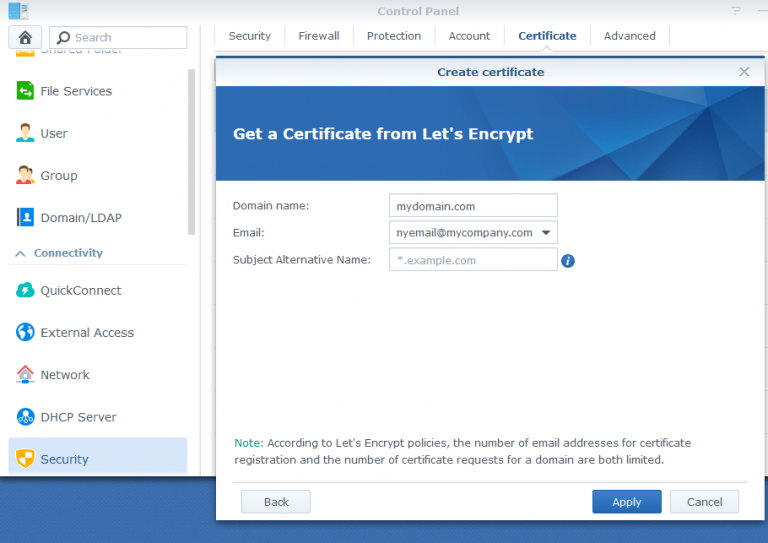
SSL certificates are required to enable websites to move from HTTP to HTTPS. It is provided by a Certificate Authority (CA). Synology NAS are configured to create certificate with Let’s Encrypt via Control Panel / Security / Certificate tab:
- Add a new certificate
- Get a certificate from Let’s Encrypt
Fill in the required information:
After a few seconds, the new SSL certificate should appear in the list with an Expiry date. Although it is set at 90 days after the creation as per Let’s Encrypt rules, the Synology NAS will auto-renew the certificate at due date.
Note
Any SSL certificate can be exported via the same Control Panel / Security / Certificate tab.
They are stored in following folder: /usr/syno/etc/certificate/_archive. You can find the subfolder for a given domain typing this command in a ssh terminal: grep -Ril “DOMAIN_NAME”